The Two Hole Duplication Methods Are Called
What are the two hole duplication methods in aviation. The part should be located on only one not both side of surfaces.

A Schematic Inverse Segmental Duplication Event In An Inverse Download Scientific Diagram
Stick it in the two-hole.
. Duplicate another term for Body double in films. B Both the hub and the flange locating the same parallal surface c Difficulty with combining hole and surface location. ASA Sheet Metal and Non-Metallic Structures.
A mimeograph machine is a low-cost duplicating machine that works by forcing ink through a stencil onto paper. Modified 6 years 2 months ago. And whenever two guidelines appear to conflict the method which most clearly communicates the size information shall prevail.
Toilet paper goes in first then poo. 9 a Flat surface can be redundantly located. Upgrade to remove ads.
B Do not dimension inside an object or have the dimension line touch the object unless clearness is gained. Problem duplication is when content copies either 1 confuse using your information or 2 obscure the ideal content. 2 hole pattern as datum.
Methods that are stored in the world are called ___ and ones that are related to an object are called _____ world methods object methods. The step drill combines these two functions into one step. In a class scope we can have only one public static void main String args per class since a static method of a class belongs to a class and not to its objects and is called using its class name.
Duplicate Scrabble a Scrabble variant popular in French and some other languages. Another name proposed by John Klumpp of Brisbane is the Eduction Method. The process is called mimeography and a copy made by the process is a mimeograph.
A The spacing between dimension lines should be uniform throughout the drawing. In attached sketch I want to have the two 752 holes located - 004 dia to each other and perpendicular to datum A 001 dia. These are designed for duplicating either threaded or unthreaded holes.
They are known by a number of names that include. Typically the procedure for drilling holes larger than 316 inch in sheet metal is to drill a pilot hole with a No. It is important when you give an example claiming that two methods are identical apart from a return statement when there are actually other differences.
When the methods are used together however they cause a duplicate condition. 2A753- EDIT 6- Volume 4 URE Questions. The method can also be used to coax stingless bees into a box from a natural nest site in a large tree or an inaccessible cavity.
This is one of a family of three-dimensional views called pictorial drawings. Close copies are the worst kind since it may be difficult to determine which is the best version. Either locational method locating from the holes or locating from the edges works well if used alone.
One end of the tool has a sharp point located in the center. Ask Question Asked 6 years 2 months ago. Avoid over-dimensioning a part.
Dont be too narrow in thinking about duplication exact copies are not as serious as other kinds of copies. Then these two holes become datum B to locate the 252 dia hole. Alice then copies the statement.
Asked By Wiki User. 30 drill bit and then to oversize with a larger drill bit to the correct size. We pass messages to the objects through methods.
Even with the edit thats the case. Lists all of the objects methods. This is necessary for the duplication process of DNA called Replication.
Double dimensioning of a feature is not permitted. The shoulder of a leader should begin anywhere within the note TF False. 200 feet off trail campsite or water source 70 steps and out of the way of water runoff.
They are sized for the diameter of the hole you need duplicated. When manufacturing a section of sheet metal for replacement using the old section as a template you should drill the rivet holes in the new sheet in what direction. You can also add more than one.
For counting the duplicates you can use Underscorejs which has a method called _groupByIt gives you an object of key-value pairs where keys are the value you want to check for duplication and value is the array of objects what have that key. Duplicate bridge a popular variant of contract bridge. No information is sent back and forth.
Decouple duplicate discriminate the three Ds articulated by Madeleine Albright as necessary for NATO to avoid. 4- Duplicate locators Redundant or duplicate locators should be avoided. Blind hole spotter transfer pin transfer screw or hole locating transfer punch.
Architectural and structural drawings should hold to the dimensioning rules and procedures identified in this chapter TF False. How to avoid code duplication inside two methods. I call the two-hole.
See more words with the same meaning. Alternatively pack toilet paper out. Mimeographs along with spirit duplicators and hectographs were common technologies for printing small quantities of a document as in office work classroom.
The representation of the object in figure 2 is called an isometric drawing. They have now been replaced by digital duplicators scanners laser printers and photocopiers but for many years they were the primary means of reproducing documents for limited-run distributionThe duplicator was pioneered by Thomas Edison and David Gestetner with. 6 to 8 inches deep 4-6 inches in diameter mix ingredients with a stick cover with organic matter not rock and disguise with natural materials.
Dimensions should be easy to read and minimize the possibility for conflicting interpretations. The example at c shows the difficulty with combining hole and surface location. The condition may result in parts that cannot be loaded or unloaded as intended.
Every dimension must have an associated tolerance and that tolerance must be clearly shown on the drawing. We call this technique Natural Hive Duplication. Examples include codes generated from the users smartphone Captcha tests fingerprints.
To use the main method of Sum class we can use the class name Summainnull or Summain1Passing integer value in the DefClass main. When an aircraft skin is being replaced without the use of a template which of the following methods should never be used in marking the new skin to duplicate the rivet holes in. 2 hole pattern as datum2.
Double dimensioning is the process of placing dimensions and standard inches and millimeters TF False. This method was first shown to us by Tom Carter of Rockhampton. In an isometric drawing the objects vertical lines are drawn vertically and the horizontal lines in the width and depth planes are shown at 30 degrees to the horizontal.
Duplicating machines were the predecessors of modern document-reproduction technology. Multi-Factor Authentication MFA is an authentication method that requires two or more independent ways to identify a user.

The Duplication Cycle Of The Spspb The Illustrations Indicate The Download Scientific Diagram

The Duplication Cycle Of The Spspb The Illustrations Indicate The Download Scientific Diagram

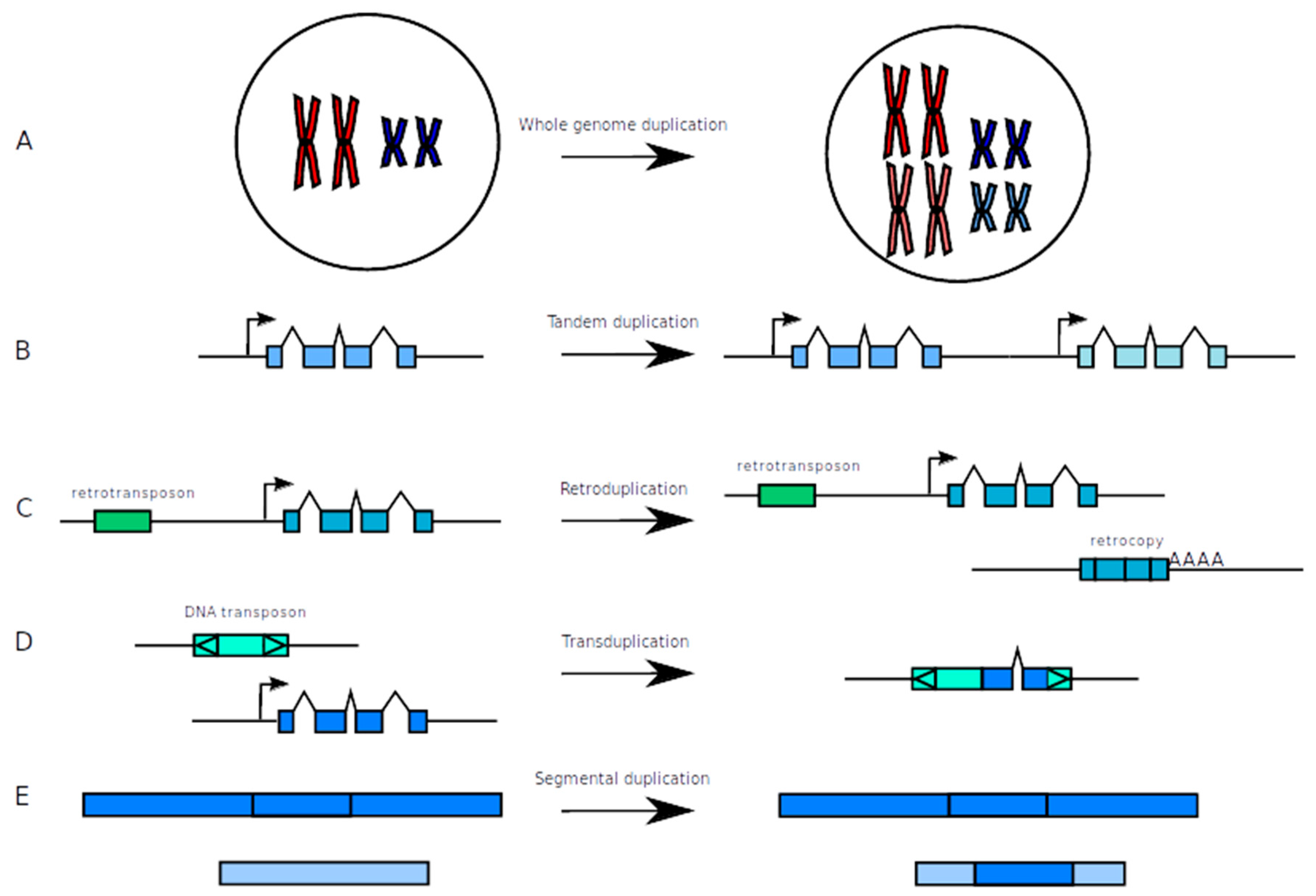
Genes Free Full Text An Overview Of Duplicated Gene Detection Methods Why The Duplication Mechanism Has To Be Accounted For In Their Choice Html

Comments
Post a Comment